The Cisco ASA 5500 security appliance is not just a plain firewall. With an add-on security module (AIP-SSM), you can transform the ASA 5500 into an IDS/IPS sensor as well.
The AIP-SSM (Advanced Inspection and Prevention – Security Services Module) is a full-blown IDS/IPS sensor with the same software and functionality like the external standalone IPS-4200 series appliance.
The Sensor operates in either “Promiscuous Mode” (IDS functionality) or “Inline Mode” (IPS functionality).
In Promiscuous Mode, the sensor does not intervene in traffic flow, but just “sniffs” the traffic that passes through the firewall and takes appropriate actions in the event of an attack.
The actions can vary from alert, TCP reset, drop the session or the whole IP communication. The IDS sensor can not take actions by itself since it is not involved inside the traffic flow.
Rather, it instructs the ASA firewall to take action to the malicious traffic using the “shun” command. The advantage of using the sensor in promiscuous mode is that it does not affect the forwarding performance of the firewall.
The disadvantage is that the promiscuous sensor can not block some types of attacks (e.g single-packet attacks) and is a little bit slow to react to attacks.
In Inline Mode, all traffic flows through the IPS sensor before or after passing through the ASA firewall. In this configuration, the IPS sensor can take action to attacking traffic by itself.
Since the inline mode operation puts the sensor directly into the traffic flow, it affects the general forwarding performance of the ASA appliance.
The advantage however of inline operation is that the sensor can stop attacks by dropping malicious traffic before it reaches the intended target, thus providing a proactive service.
The AIP-SSM plug-in module has two models:
- ASA-SSM-AIP-K9-10 (approx. 100Mbps throughput)
- ASA-SSM-AIP-K9-20 (approx. 200Mbps throughput)
The figure below shows how the AIP-SSM module can be installed inside a Cisco ASA appliance:
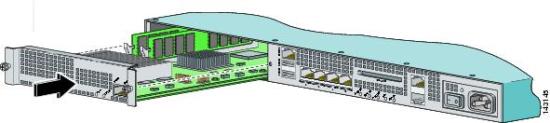
After inserting the module in the appliance, you can verify that is properly installed with the
ASA# show module 1 command. If the status reads UP, AIP-SSM is properly installed.
To remove the module while it operates, you have to shut it down first using:
ASA# hw-module module 1 shutdown.
After that, you have to power off the ASA and then remove the AIP-SSM module.
Similarly, to reboot the module for any reason use:
ASA# hw-module module 1 reset
ASA Models that support IPS Module (AIP-SSM):
As we mentioned above, the Cisco ASA 5500 appliance supports an Intrusion Detection/Intrusion Prevention plug-in module (AIP-SSM).
However not all models support this. Specifically only the middle-range models support it. The lowest-end model (5505) and the highest-end models (5550, 5580) does not support the AIP-SSM IPS module.
The following models support the IPS module device:
- Cisco ASA 5510
- Cisco ASA 5520
- Cisco ASA 5540
Basically the ASA 5505 can not support the AIP-SSM because of its small size. Also, the 5550 can not support the module because its hardware is occupied with much more integrated network ports compared with other models (it has 8-10/100/1000 and 4 gigabit SFP ports).
The highest-end 5580 does not support the module because an IPS inline module in the 5580 would decrease its packet forwarding performance (remember that the 5580 is usually used in high traffic environments).
How to Upgrade AIP-SSM on ASA
I have recently upgraded a few Intrusion Prevention System (IPS) modules which are embedded in ASA firewalls. The IPS models are AIP-SSM-20 which were upgraded from version 5.1 to 6.0
The AIP-SSM module can be accessed either through the ASA CLI (using “session 1” ) command, or via its dedicated management interface using SSH.
I have already assigned an IP address to the IPS management interface, so I did all the upgrade via the management interface. You need also an FTP server to host the upgrade image files.
Lets see how to upgrade the AIP-SSM IPS module below:
FTP server address: 172.20.1.8
Upgrade file used: IPS-K9-6.0-1-E1.pkg (major upgrade from 5.1 to 6.0)
Signature upgrade file: IPS-sig-S338-req-E1.pkg
Note about signature files: the keyword “req-E1” in the signature filename means that it requires an E1 signature engine software installed.
After you log in to the sensor, use the “show ver” command to verify your current image version:
IPS# sh ver
Application Partition:Cisco Intrusion Prevention System, Version 5.1(5)E1
Then upgrade using the “upgrade” command:
IPS# conf t
IPS(config)# upgrade ftp://[email protected]/IPS-K9-6.0-1-E1.pkg
Password: **********
Warning: Executing this command will apply a software update to the application partition. The system may be rebooted to complete the upgrade.
Continue with upgrade? []: yesBroadcast Message from root@IPS
(somewhere) at 15:26 …Applying update IPS-K9-6.0-1-E1.pkg. IPS applications will be stopped and system will be rebooted after upgrade completes .
Broadcast Message from root@IPS
(somewhere) at 15:26 …Shutting down IPS applications. Applications will be restarted when update is complete..
IPS(config)#
***
***
*** Termination request from cids
***
Sensor is shutting down.This CLI session will be terminated
The sensor reboots by itself. Wait a few minutes and then log in again.
IPS# sh ver
Application Partition:Cisco Intrusion Prevention System, Version 6.0(1)E1
As you can see the image is upgraded successfully. Now we need to upgrade the signature file as well.
IPS# conf t
IPS(config)# upgrade ftp://[email protected]/IPS-sig-S338-req-E1.pkg
Password: **********
Warning: Executing this command will apply a signature update to the application partition.
Continue with upgrade? []: yesBroadcast Message from root@IPS
(somewhere) at 16:40 …Applying update IPS-sig-S338-req-E1
Broadcast Message from root@IPS
(somewhere) at 16:42 …Update complete
IPS(config)#
Related Posts
- What is Cisco ASA Firewall – All you need to Know
- Traffic Rate and Bandwidth Limiting on Cisco ASA Firewall
- Cisco ASA Firewall (5500 and 5500-X) Security Levels Explained
- Cisco ASA 5505-5510-5520-5540-5550-5580 Performance Throughput and Specs
- Password Recovery for the Cisco ASA 5500 Firewall (5505,5510,5520 etc)