Ever since the first modern desktop computers began appearing in offices in the 1980s, software companies have battled for supremacy. After all, a computer’s only as useful as the software running on it. That fight for dominance—and the ensuing success of the Windows operating system and the eponymous Office suite—turned Microsoft into a corporate juggernaut […]
Verizon Number Lock – Description with Pros and Cons
The security and safety of your mobile phone and confidential data are paramount. Today we rely on our smartphone to connect to our bank and manage our money, to authenticate to critical online services, to manage our social media and so much more. All it takes is a scammer to collect details from your phone, […]
15 Examples of Peripheral Devices in Computers (with Pictures and Description)
One of the most exciting things about computers is their nearly limitless potential. You can use computers to perform office work, model construction projects, create beautiful art, enable machine learning, play games, and so much more. A computer’s flexibility is usually leveraged through software. If you want to try a new task you download and […]
Main Advantages and Disadvantages of Infrastructure as a Service (IaaS)
As technology is rapidly developing, the demand for cheaper and more secure ways of accessing, processing and storing data is increasingly becoming a necessity. Infrastructure as a Service (IaaS) is a form of cloud computing service that enables organizations to access a range of computing elements remotely, like servers, networking, data storage, virtual machines etc. […]
10 Main Pros and Cons of BYOD (Bring Your Own Device) in Business
These days, desktop computers, laptops, and other digital devices are standard equipment for many businesses’ employees. However, most employees also carry an array of personal devices like smartphones and tablets everywhere they go. In the interest of simplicity, plenty of workers try to convince their employers to let them use their personal devices for work. […]
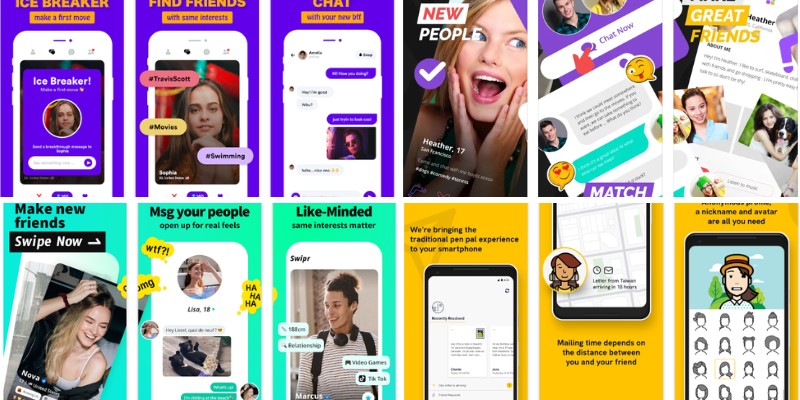
15 Apps Like Yubo (Alternatives) For Making New Friends Online
One of the best things about the Internet is how it can bring people together and even foster entirely new communities and friendships. That concept has been taken to even greater heights thanks to mobile apps like Yubo. Yubo integrates cutting-edge technologies like facial recognition and video chat to help people make real connections with […]
Here are the Main Pros and Cons of Cyber Security for Businesses
Businesses today face a daunting cybersecurity challenge. With almost every aspect of the average business’s operations either partially or fully digitized at this point, a single misstep risks disaster. To stay safe, businesses must take steps to safeguard their data and keep multiple threats at bay. The costs of failure are staggering. In the US, […]
Top 6 Operating Systems for Tablets – Description and Characteristics
Mobile devices, such as smartphones and tablets, tend to blend into each other at first glance, especially when it comes to the Operating System (OS) that runs on such devices. Regarding hardware components, you’ll typically find an ARM processor, a touchscreen interface, and a moderately powerful graphics processing unit. But there are often a lot […]
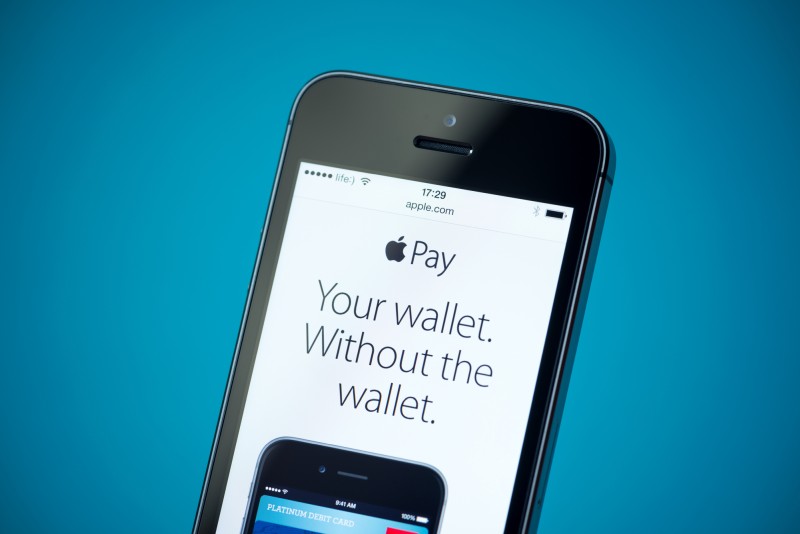
Main Advantages and Disadvantages of Apple Pay
Technology has accelerated to new heights in the last few decades, and many daily tasks have been modernized. On the cutting edge of innovation, Apple has made strides to add convenience, portability, and security into its products and software. One of the tech giant’s contributions addresses the future of payments and offers a streamlined method […]
What Does TFW Mean on My iPhone? – Which Carrier is TFW?
No one could have guessed just how dramatically the iPhone would transform the world when it was first introduced back in 2007. With each passing year, Apple has refined its hardware and software with new iPhone models, operating systems, and capabilities. For the average Apple user, keeping up with all the new terminology can be […]